Parameter tampering is a type of security vulnerability where an attacker manipulates parameters exchanged between client and server to gain unauthorized access, modify data, or execute unintended actions. This attack typically targets web applications by altering the values of parameters, such as form fields, URL query strings, cookies, or hidden fields, to bypass security mechanisms.
Practical Examples of Parameter Tampering
- Price Manipulation in an E-Commerce Website:
- Scenario: An online shopper adds an item to their cart that costs $100. The price is stored as a hidden field in the form.
- Tampering: The attacker inspects the form field using browser developer tools, modifies the price from $100 to $1, and submits the form.
- Impact: If the server does not validate the price on the backend, the attacker could purchase the item for $1, causing financial loss to the business.
- Elevating User Privileges:
- Scenario: A web application uses URL parameters to identify the user’s access level. For example, a URL like
http://example.com/admin?role=usergrants access to user-level pages. - Tampering: An attacker changes the
role=userparameter torole=adminin the URL. - Impact: If the server-side code does not properly validate user roles, the attacker could gain unauthorized access to admin functionalities, leading to potential data breaches or system compromise.
Mitigation Strategies
- Server-Side Validation: Always validate and sanitize input on the server side, regardless of client-side checks.
- Use of Secure Protocols: Implement secure communication protocols like HTTPS to encrypt data in transit and prevent interception.
- Session Management: Use secure session management practices to ensure that critical information is not exposed or manipulated through parameters.
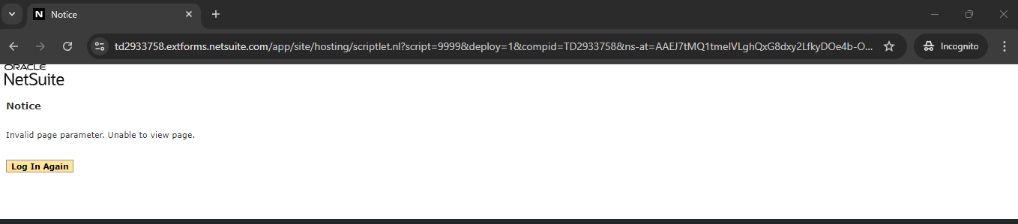
Real Practices -> URL Tampering
- Project List Page URL -> https://td2933758.extforms.netsuite.com/app/site/hosting/scriptlet.nl?script=1748&deploy=1&compid=TD2933758&ns-at=AAEJ7tMQ1tmeIVLghQxG8dxy2LfkyDOe4b-OxZA8MVMWsmEbDgs
Original: script=1748
Tampered: Change it to a non-existent or different script ID, e.g., script=9999 or script=1749.
- Edit Contact Record Page URL -> https://td2933758.extforms.netsuite.com/app/site/hosting/scriptlet.nl?script=1732&deploy=1&compid=TD2933758&ns-at=AAEJ7tMQ1_qCv2bxeR-o-LLXth5m74jKXytlDfDnj86m_zeTA2M&internalid=227
Original: script=1732
Tampered Example: Change to script=9999 (non-existent script) or remove it entirely.